Dangling DNS is a common misconfiguration issue in Domain Name System (DNS) records that can expose organizations to serious security risks, including subdomain takeover attacks.
It occurs when a DNS record points to an external service or resource that no longer exists, but the DNS entry itself remains active. Attackers can exploit this situation to gain control over unused subdomains and perform malicious activities.
What is Dangling DNS?
DNS translates human-readable domain names (like example.com) into IP addresses.
Sometimes organizations configure DNS records to point to third-party services, cloud providers, or content delivery networks (CDNs). If these services are later removed or expired but the DNS record is not deleted, the domain is said to be ‘dangling.’
The result? The DNS record still exists — but it points to something that’s no longer there.
The danger? Attackers can claim that unused resources and take control of your subdomain
Examples of Dangling DNS
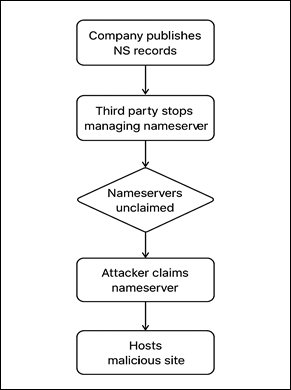
Example 1: Subdomain Takeover Using NS Record
- Setup: partners.example.com is delegated to a separate DNS server using an NS record as below:
partners.example.com. IN NS ns1.thirdparty-dns.com.
partners.example.com. IN NS ns2.thirdparty-dns.com.
*These NS records point to a DNS service managed by a third-party vendor.
- Vendor Change: Later, the vendor stops managing DNS for partners.example.com and releases the nameservers ns1.thirdparty-dns.com and ns2.thirdparty-dns.com.
Dangling Delegation: The NS records still exist in example.com’s DNS, but the target nameservers are unclaimed or expired.
- Attacker Action: The attacker registers thirdparty-dns.com, sets up their own DNS servers as ns1.thirdparty-dns.com and ns2.thirdparty-dns.com.
They now control DNS resolution for partners.example.com.
- Impact:
- Attacker can point partners.example.com to malicious IPs or phishing servers.
- Visitors, email traffic, or APIs using partners.example.com go through attacker-controlled DNS.
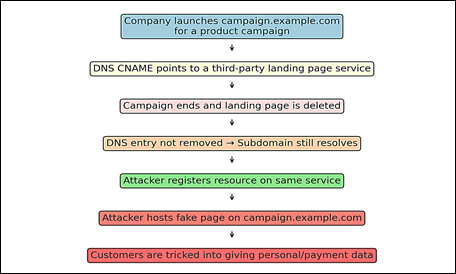
Example 2: Marketing Campaign Subdomain
A company launches campaign.example.com website for a three-month product campaign using a third-party landing-page service (like Unbounce, HubSpot, or WordPress hosting).
- The DNS points to the service using a CNAME record.
- When the campaign ends, the marketing team deletes the landing page but forgets to remove the DNS entry.
Now, campaign.example.com still exists in DNS but no longer leads to any real page.
An attacker signs up on the same service and claims the abandoned resource.
They host a fake page under campaign.example.com, tricking customers into entering personal or payment information.
This kind of dangling DNS misconfiguration is one of the most common ways attackers perform subdomain takeover on websites.
Types of Dangling DNS Based on Record Misconfigurations
1. CNAME Record Dangling DNS (Most Common)
- What happens: A CNAME record points a subdomain (e.g., shop.example.com) to an external service (like AWS, Azure, GitHub Pages). If the resource is deleted but the DNS entry stays, the subdomain becomes “dangling.”
- Risk: Attackers can register the same resource on the service and take control of the subdomain.
- Impact: High — frequently used for subdomain takeover attacks.
2. A / AAAA Record Dangling DNS
A records map a domain to an IPv4 address, while AAAA records map a domain to an IPv6 address.
- What happens: An A (IPv4) or AAAA (IPv6) record points to an IP address that is no longer owned by the company (e.g., released from cloud hosting).
- Risk: If that IP is reassigned to someone else, they can control your subdomain’s content or serve malicious content.
- Impact: High — less common than CNAME takeovers but still possible.
3. NS Record Dangling DNS
- What happens: A subdomain is delegated to a nameserver using an NS record, but that nameserver domain is no longer valid or has expired.
- Risk: Attackers can register the expired nameserver domain, gain DNS control of the subdomain, and redirect traffic to attacker’s environment.
- Impact: High — can compromise all records under that subdomain
Subdomain Takeover as a Result of Dangling DNS
What is Subdomain Takeover?
Subdomain takeover is an attack where cybercriminals gain control of a subdomain that points to an unclaimed or expired resource.
How it works: When CNAME, A, or NS records point to non-existent resources, attackers claim those resources and “take over” the subdomain.
Why is this bad?
- They can make it look completely legitimate.
- They can Phish Users
- Impersonate the legitimate company to steal sensitive information.
- They can spread malicious files or host malicious content.
- Victims trust the domain because it belongs to a real company.
How to Prevent Dangling DNS
To protect against dangling DNS and subdomain takeover attacks, organizations should:
– Use automated tools like Progist Dangling DNS to detect dangling DNS records and receive respective alerts.
– Regularly audit DNS records and remove unused or outdated entries.
– Ensure cloud services and third-party resources are properly decommissioned
– Implement strong access control and monitoring on DNS management systems.
Conclusion
Dangling DNS is a simple yet dangerous misconfiguration that can lead to subdomain takeover attacks. By maintaining proper DNS hygiene and performing regular audits, organizations can significantly reduce this risk and protect their domains from being hijacked and prevent exposure of sensitive data.
Need Help Securing Your DNS?
At Progist, we’ve been helping organizations identify and fix critical DNS misconfigurations like dangling DNS records before attackers can exploit them. Whether you need help with:
- Detecting and mitigating dangling DNS vulnerabilities
- Strengthening SPF, DKIM, and DMARC configurations
- Monitoring domain abuse and ensuring DNS hygiene
we’re here to assist.
📩 Get in touch: info@progist.net
📞 Call us at: +91-9820116312 | +91-9819256263
Let’s make sure your DNS is secure, not just compliant, but resilient against real threats.

