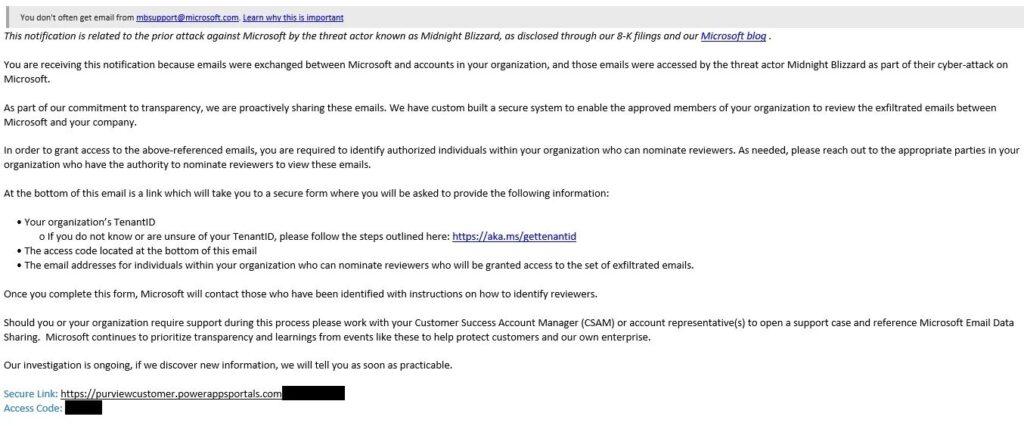
In a recent and notable incident, Microsoft found itself at the center of an email security debacle when their data breach notification emails were flagged as spam by their own security systems. This mishap affected Microsoft 365 customers, who discovered these critical notifications relegated to their spam or junk folders, raising concerns about email authentication practices and the proper implementation of DMARC protocols.
What Went Wrong?
The crux of the issue lay in the improper deployment of DMARC (Domain-based Message Authentication, Reporting & Conformance) protocols. DMARC, in conjunction with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), is designed to authenticate emails and prevent spoofing. When an email fails these checks, the DMARC policy determines if it should be marked as spam or rejected entirely. To understand how SPF, DKIM, and DMARC work together to authenticate email message senders, check out our detailed blog post.
In Microsoft’s case, several factors contributed to the misclassification of their breach notifications:
- High-Level Account Information Requests: The emails asked for sensitive account information, raising red flags.
- Ambiguous Links: The included links were not clearly associated with Microsoft, which is a common characteristic of phishing emails.
- DMARC Implementation Issues: There were flaws in the way DMARC protocols were configured, leading to failures in email authentication.
This issue was first brought to light by Kevin Beaumont, a renowned security researcher. He flagged the problem in a LinkedIn post, which quickly gained traction and was shared over 1,900 times. Beaumont’s timely intervention highlighted the gravity of the situation and underscored the need for rigorous email security measures. One LinkedIn user commented on the post:
“Several of my clients received this email. All of them were worried it was phishing, since no SPF & DKIM were used according to the email headers and the URL mentioned in the email message was hosted as a simple (almost dummy) Azure PowerApp with a simple DV SSL certificate issued by another trusted CA and without any organization info (all other MS domains have OV/EV certificates issued by Microsoft as a publicly trusted CA)…weird way for a provider like this to communicate an important issue to potentially affected customers.”
The Implications
This incident underscores the importance of correctly configuring email authentication protocols. For organizations, it serves as a reminder that even industry giants are not immune to such lapses, and the consequences can be significant. Misclassified emails can lead to missed critical communications, resulting in security vulnerabilities and loss of trust.
How ProDMARC Can Help
At Progist, we understand the complexities and challenges associated with email authentication. As Asia’s leading DMARC service provider, our ProDMARC tool offers comprehensive DMARC analysis and reporting, helping organizations secure their email communications effectively.
With ProDMARC, you can:
- Ensure Proper DMARC Implementation: Our tool provides detailed insights and recommendations for configuring DMARC, SPF, and DKIM protocols correctly.
- Monitor and Analyze Email Traffic: Gain visibility into your email ecosystem with detailed DMARC reports on authentication results and potential security issues.
- Prevent Email Spoofing and Phishing: Protect your domain from spoofing attacks and ensure that your emails are trusted and authenticated.
Don’t let your organization fall victim to email security lapses. Ensure your email communications are secure and trusted with ProDMARC. Contact us today at +91-9820116312 or book a demo to learn more about how our DMARC tool can safeguard your domain and enhance your email security posture.

